Java反序列化漏洞简单理解
b0c58e74f05693590a5e95bae0ac94a8bdf14f5a1d7af15015feb34db539a2213edee1c25b686ab99749e964814cb5c5b134b5b870125a928192930fe8ce484695c57541da153038aa86194099c8e4c7aeb33c0ba49aed29f4aaad800ad2c95217984089f1bcb99a303a1130d3a7699e6a30fe68b02cb6987a9ca9a2ee18baa3f107398780083375754ea99494ec6237645894fe05ccfc6578f88ea538618c04e7c63bd76192a6af377ff49331d9e25d238522b3195da2e92680d5badffd0b61e362b6b90a773bb4d4baf5f77f518576d867f1da92c7e6965695f928d4608272416bfbd83761890430cd2cc69d63a58fa4aaf1f07d0886e64 ...
CC1中反射调用的构造
b0c58e74f05693590a5e95bae0ac94a8bdf14f5a1d7af15015feb34db539a2213edee1c25b686ab99749e964814cb5c5b134b5b870125a928192930fe8ce484695c57541da153038aa86194099c8e4c7aeb33c0ba49aed29f4aaad800ad2c95217984089f1bcb99a303a1130d3a7699e6a30fe68b02cb6987a9ca9a2ee18baa3f107398780083375754ea99494ec6237645894fe05ccfc6578f88ea538618c04e7c63bd76192a6af377ff49331d9e25d238522b3195da2e92680d5badffd0b61e362b6b90a773bb4d4baf5f77f518576d867f1da92c7e6965695f928d4608272416bfbd83761890430cd2cc69d63a58fa4aaf1f07d0886e64 ...
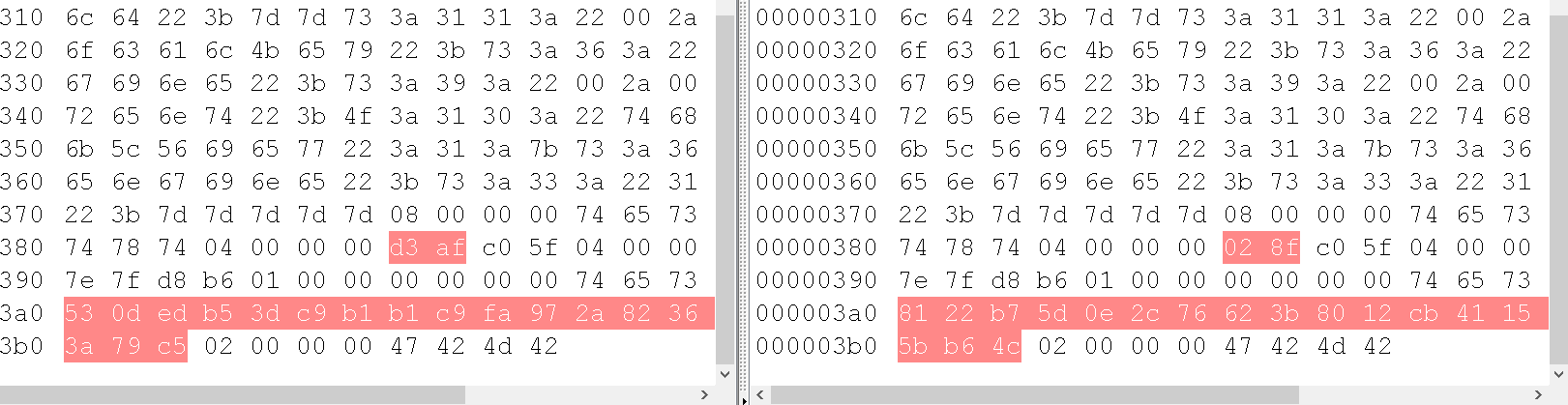
Phar文件记录
b0c58e74f05693590a5e95bae0ac94a8bdf14f5a1d7af15015feb34db539a2213edee1c25b686ab99749e964814cb5c5b134b5b870125a928192930fe8ce484695c57541da153038aa86194099c8e4c7aeb33c0ba49aed29f4aaad800ad2c95217984089f1bcb99a303a1130d3a7699e6a30fe68b02cb6987a9ca9a2ee18baa3f107398780083375754ea99494ec6237645894fe05ccfc6578f88ea538618c04e7c63bd76192a6af377ff49331d9e25d238522b3195da2e92680d5badffd0b61e362b6b90a773bb4d4baf5f77f518576d867f1da92c7e6965695f928d4608272416bfbd83761890430cd2cc69d63a58fa4aaf1f07d0886e64 ...